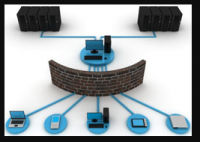
An Intrusion Detection System (IDS) is a machine that monitors community visitors for suspicious hobby and troubles alerts whilst such hobby is found. It is a software utility that scans a community or a machine for dangerous activity or coverage breaching. Any malicious challenge or violation is generally reported both to an administrator or gathered centrally the use of a safety data and event control (SIEM) gadget. A SIEM system integrates outputs from more than one assets and makes use of alarm filtering techniques to distinguish malicious hobby from false alarms.
Intrusion Detection System (IDS)
An Intrusion Detection System (IDS) is a machine that monitors community visitors for suspicious hobby and troubles alerts whilst such hobby is found. It is a software utility that scans a community or a machine for dangerous activity or coverage breaching. Any malicious challenge or violation is generally reported both to an administrator or gathered centrally the use of a safety data and event control (SIEM) gadget. A SIEM system integrates outputs from more than one assets and makes use of alarm filtering techniques to distinguish malicious hobby from false alarms.
Although intrusion detection systems display networks for potentially malicious hobby, they are also disposed to false alarms. Hence, corporations need to great-track their Intrusion Detection Systems in Tysons Corner merchandise when they first install them. It method nicely putting in place the intrusion detection structures to recognize what normal traffic on the community seems like as compared to malicious activity.
Intrusion prevention systems also screen community packets inbound the device to check the malicious activities concerned in it and right now sends the caution notifications.
Classification of Intrusion Detection System:
IDS are categorized into five sorts:
Network Intrusion Detection System (NIDS):
Network intrusion detection structures (NIDS) are installation at a deliberate point within the community to have a look at traffic from all devices on the network. It performs an commentary of passing visitors on the whole subnet and suits the traffic that is surpassed at the subnets to the gathering of known attacks. Once an attack is identified or unusual behavior is observed, the alert may be sent to the administrator. An instance of an NIDS is putting in it on the subnet where firewalls are located with the intention to see if a person is trying crack the firewall.
Host Intrusion Detection System (HIDS):
Host intrusion detection structures (HIDS) run on independent hosts or devices on the community. A HIDS video display units the incoming and outgoing packets from the tool simplest and will alert the administrator if suspicious or malicious activity is detected. It takes a picture of current gadget documents and compares it with the previous photo. If the analytical gadget files have been edited or deleted, an alert is sent to the administrator to analyze. An instance of HIDS utilization may be visible on assignment important machines, which aren't expected to exchange their layout.
Protocol-based totally Intrusion Detection System (PIDS):
Protocol-based totally intrusion detection device (PIDS) accommodates of a machine or agent that could continuously resides on the front cease of a server, controlling and interpreting the protocol among a consumer/tool and the server. It is trying to secure the internet server through frequently tracking the HTTPS protocol circulation and receive the related HTTP protocol. As HTTPS is un-encrypted and earlier than immediately getting into its internet presentation layer then this system would want to live in this interface, among to apply the HTTPS.
Application Protocol-primarily based Intrusion Detection System (APIDS):
Application Protocol-based totally Intrusion Detection System (APIDS) is a device or agent that usually resides inside a set of servers. It identifies the intrusions through monitoring and decoding the communication on utility unique protocols. For example, this will monitor the SQL protocol express to the middleware as it transacts with the database inside the internet server.
Hybrid Intrusion Detection System :
Hybrid intrusion detection device is made through the aggregate of two or more procedures of the intrusion detection device. In the hybrid intrusion detection system, host agent or gadget records is mixed with network statistics to broaden a whole view of the network machine. Hybrid intrusion detection machine is more powerful in contrast to the opposite intrusion detection device. Prelude is an instance of Hybrid IDS.






*********22@gmail.com
Sincerely, I appreciate how easy on the eyes it is. I'd like to know how to be notified whenever a new post is made happy wheels.