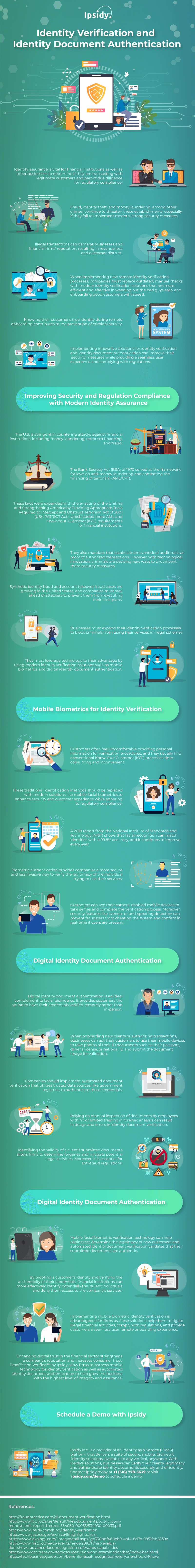
These advanced identity proofing technologies ensure companies that they only interact with legitimate individuals. For more information on the matter, Ipsidy provides the following infographic.
Enterprises across various industries are becoming more reliant on digital technology. Trends and practices are continually shifting, and companies must keep up with these changes. Through digital transformation, firms can streamline their operations, improve productivity, and provide better services to their customers. It can also help them improve their market position.
Although technological innovation is well-intentioned, fraudsters are using these modern tools to exploit services. Their illicit tactics are becoming more sophisticated as they try to find vulnerabilities in systems. Identity theft, financial scams, and other crimes continue to jeopardize organizations, especially those who still implement inefficient security protocols.
Many establishments still rely on outdated identity verification methods like knowledge-based authentication (KBA) to confirm their customers’ identities. Since this identity proofing process relies on easily stolen information, criminals can quickly circumvent them and infiltrate the network.
These conventional verification procedures do not authenticate the person’s claimed identity and only confirm if they know the required information. A criminal’s success starts when they get past onboarding. Therefore, institutions must deploy robust identity verification for remote onboarding like mobile facial biometric identity authentication to stop fraudsters from the very beginning.
This identity proofing technology has become one of the most trusted methods to prove that the person is who they claim to be. It is easy to implement and convenient to use as it leverages commonly available mobile devices to perform the authentication process.
It also has additional features and controls to ensure that a real person is initiating the action. Users will be asked to undergo an active liveness check by performing gestures known only at the time of authentication, such as blinking, smiling, or moving their head. This technology is difficult to cheat as it can detect inconsistencies on the live image, denoting possible signs of fraud.
Institutions can also implement an automated identity document authentication to ensure that the government-issued credential provided by the user is genuine. This digital solution leverages integrated optical character recognition (OCR) document capture to scan the ID to determine if it has the markings of a legitimate government-issued credential. Authentic IDs often have security markings that help to distinguish them from fake ones.
Using modern and strong identity verification technology and partnering with the right Identity as a Service provider enable companies to prevent losses and increase revenue. However, with many such firms offering IDaaS, choosing the right one can be challenging. They must select the ideal partner who can cater to their security needs.
Businesses must ensure that they are transacting with legitimate persons. The ability of firms to safeguard their network from fraudulent attacks greatly affects their performance in the industry. Failure to do so also entails considerable costs, including financial losses, customer distrust, and brand damage. Furthermore, they might also get penalized for failing to comply with regulatory standards.
Identity verification and identity document authentication play a crucial role in protecting the network and helping companies exercise due diligence to regulatory compliance. For more information about the matter, an infographic from Ipsidy is provided below.